A Biased View of Disaster Recovery
as the name suggests, Locky is what it does (locks you out of documents and changes the data with the expansion. lockey). Its name misses the most damaging component of this kind of ransomware its rate. Locky has the difference of spreading out to other documents throughout the network much faster than various other ransomware pressures.
The Disaster Recovery Statements
The significance of this facet of the assault is that it qualifies as a violation if your business collaborates with personal data; companies must get in touch with anyone that may have information on your network to remain in compliance with neighborhood, state, and also government guidelines. assaults unpatched Wild, Fly application servers in the internet-facing section of their network.
attacks the database web server procedures to access rather of going directly after the data. Its creators sell the ransomware software application to offenders for a part of the ransom accumulated, i. e., Ransomware-as-a-Service. is a variation of ransomware standing for the trend in what is called "leakware." After information is encrypted, negative actors endanger to leak ransomed personal data on the dark internet unless the ransom is paid.
The Disaster Recovery Ideas
: An innovation in which information is equated right into an unreadable type or code, as well as just customers with access to a secret key or password can read it. File encryption at rest and in-flight makes sure the back-up information, also if exfiltrated, is provided ineffective to criminals without the decryption secrets or password.
Information protection entails numerous layers of defense that are not restricted to the app itself: the host level, the operating system level, the user level, the manager degree, and also also the physical level of the device all have vulnerabilities that a good safety and security system must address. For this factor, application solidifying may be called system solidifying or OS hardening.
The 10-Second Trick For Disaster Recovery
When calamity strikes there is usually some downtime that includes it as employees work to recover information and get systems back up and also running - disaster recovery. Downtime normally comes with shed profits due to the fact that workers can not concentrate on their everyday income generating tasks. use this link Keeping consumers happy as well as coming back for even more is the top top priority of every company and also in this hectic globe we live in, consumers anticipate perfection.
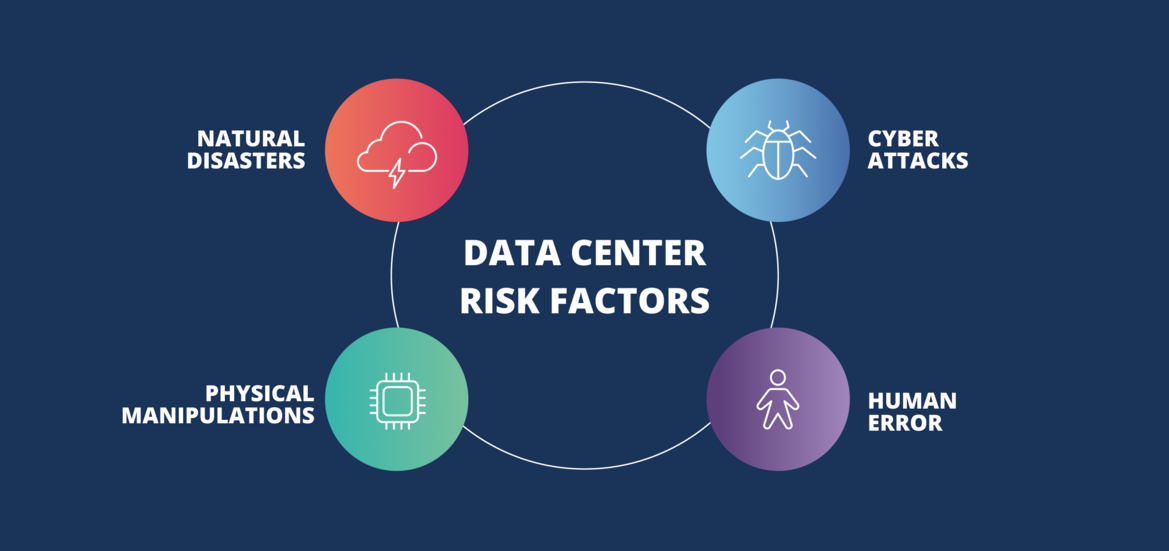
Disaster healing preparation is a vital procedure for every company to go through. A disaster recovery strategy calls for recognizing threats, setting goals of disaster recovery, researching the finest means to attain those goals, and also testing the strategy.
7 Easy Facts About Disaster Recovery Explained
Organizations needs to have a positive strategy to handle supply chain disruption triggered by cybersecurity occasions. Supply chains often are an internet of inner and also outside business procedure interdependencies with essential vendors in scope. Therefore, service continuity planning as well as disaster recuperation methods ought to think about the impact of cybersecurity hazards and also risks throughout the supply chain.
A cyberattack draws in much much more media attention, subjecting your company and also its stakeholders to higher Clicking Here risks of reputational damages. It is frequently a stress cooker when senior administration, legal, and also the press all desire answers that you may or might not be able to supply (and some responses that you need to not provide).
The 6-Minute Rule for Disaster Recovery

Below are a couple of things to think about throughout the business continuity planning as well as disaster recovery approach advancement process: Designate an Inner Interaction Lead or provide that function and duty to existing management, such as an Incident Response Supervisor. Make sure the entire company recognizes who he or she is as well as delays to them in a dilemma situation (disaster recovery).
There is much to take into consideration when believing concerning how cybersecurity effects business connection preparation and catastrophe healing methods. Proactively including these essential points will certainly go a lengthy method to decreasing the damages as well as speeding healing.
How Disaster Recovery can Save You Time, Stress, and Money.

A disaster recuperation strategy is even more than simply restoring data; it additionally assists to recreate the organization's entire IT system, consisting of information, networks as well as applications, so that there's no loss of performance for extensive time periods. Catastrophe recuperation also moves any information from the short-term setting to the primary one as soon as back up and running.
Disaster Recovery Fundamentals Explained
A service continuity strategy is a thorough strategy that makes sure the processes and also systems within an organization continue also if unintended situations make this hard. The demand for a connection plan has actually become also much more important as cybercrime remains to progress as well as become more sophisticated, implying companies require to be a lot more aggressive in securing their operations.